资料:https://cert-manager.io/docs/configuration/acme/#creating-a-basic-acme-issuer
~~~bash
# Kubernetes 1.16+
$ kubectl apply -f https://github.com/jetstack/cert-manager/releases/download/v1.1.0/cert-manager.yaml
# Kubernetes <1.16
$ kubectl apply --validate=false -f https://github.com/jetstack/cert-manager/releases/download/v1.1.0/cert-manager-legacy.yaml
~~~
**环境:k8s1.18.3,cert-manager v0.15.1,集群必须已经装有 Ingress Controller**
cert-manager+nginx-ingress+letsencrypt的免费套餐
官方网站:https://cert-manager.io/docs/faq/acme/
## 1. Installing with regular manifests
`wget https://github.com/jetstack/cert-manager/releases/download/v0.15.1/cert-manager.yaml`
## 2. configuration
参考:https://cert-manager.io/docs/configuration/acme/
创建一个签发机构,使用ACME的Let’s Encrypt自动管理证书
letsencrypt提供免费的SSL证书
配置`staging`环境使用的 Let‘s Encrypt ClusterIssuer,并创建:
```
apiVersion: cert-manager.io/v1alpha2
kind: ClusterIssuer
metadata:
name: letsencrypt-staging
spec:
acme:
# You must replace this email address with your own.
# Let's Encrypt will use this to contact you about expiring
# certificates, and issues related to your account.
email: tony@lwork.com
server: https://acme-staging-v02.api.letsencrypt.org/directory
privateKeySecretRef:
# Secret resource that will be used to store the account's private key.
name: letsencrypt-staging
# Add a single challenge solver, HTTP01 using nginx
solvers:
- http01:
ingress:
class: nginx
```
配置`production`环境使用的 Let‘s Encrypt ClusterIssuer,并创建:
```
apiVersion: cert-manager.io/v1alpha2
kind: ClusterIssuer
metadata:
name: letsencrypt-prod
spec:
acme:
# You must replace this email address with your own.
# Let's Encrypt will use this to contact you about expiring
# certificates, and issues related to your account.
email: tony@lwork.com
server: https://acme-v02.api.letsencrypt.org/directory
privateKeySecretRef:
# Secret resource that will be used to store the account's private key.
name: letsencrypt-prod
# Add a single challenge solver, HTTP01 using nginx
solvers:
- http01:
ingress:
class: nginx
```
* metadata.name 是我们创建的签发机构的名称,后面我们创建证书的时候会引用它
* spec.acme.email 是你自己的邮箱,证书快过期的时候会有邮件提醒,不过 cert-manager 会利用 acme 协议自动给我们重新颁发证书来续期
* spec.acme.server 是 acme 协议的服务端,我们这里用 Let’s Encrypt,这个地址就写死成这样就行
* spec.acme.privateKeySecretRef 指示此签发机构的私钥将要存储到哪个 Secret 对象中,名称不重要
* spec.acme.http01 这里指示签发机构使用 HTTP-01 的方式进行 acme 协议 (还可以用 DNS 方式,acme 协议的目的是证明这台机器和域名都是属于你的,然后才准许给你颁发证书)
**这里分别配置了测试环境与生产环境两个 ClusterIssuer, 原因是 Let’s Encrypt 的生产环境有着非常严格的接口调用限制,最好是在测试环境测试通过后,再切换为生产环境。**
**letsencrypt的测试环境和生产环境的区别:** https://letsencrypt.org/zh-cn/docs/staging-environment/
## 3. 测试
参考:https://cert-manager.io/docs/usage/ingress/
**这里我假设你已安装好 Nginx Ingress Controller 并已存在一个 Ingress 对象**,现在为它开启 TLS 选项
```
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: my-nginx
namespace: crm
annotations:
kubernetes.io/ingress.class: "nginx"
kubernetes.io/tls-acme: "true"
cert-manager.io/cluster-issuer: "letsencrypt-prod"
spec:
rules:
- host: nginx.lwork.com
http:
paths:
- backend:
serviceName: my-nginx
servicePort: 80
path: /
tls:
- secretName: nginx.lwork.com
hosts:
- nginx.lwork.com
```
* 在创建第一个ingress规则的时候报错`Internal error occurred: failed calling webhook "validate.nginx.ingress.kubernetes.io": an error on the server ("") has prevented the request from succeeding`
* 处理办法`kubectl delete -A ValidatingWebhookConfiguration ingress-nginx-admission`
**之后 Cert-manager 会读取注解并创建证书,使用以下命令查看:**
**会自动创建certificate,会自动http跳转https**
```
kubectl get certificate -n crm
NAME READY SECRET AGE
test-nginx-tls False test-nginx-tls 32m
```
**当 Ready 为 True 时代表证书安装成功**
# Troubleshooting
若出现问题参考 :https://cert-manager.io/docs/faq/acme/ 下的 **Troubleshooting Issuing ACME Certificates**
首先查看cert-manager日志
### **cert-manager+nginx-ingress+letsencrypt的几种简单架构**
一、启用slb监听80和443端口,slb启用一个虚拟服务器指向k8s所在的服务器监听后端端口57997(这个端口是目前ingress-nginx的svc监听443的端口),然后域名解析地址修改到这个slb
1. 默认已有ingress-nginx,cert-manager和测试用的后端服务。
`ingress-nginx-controller NodePort 10.101.133.55 <none> 80:25385/TCP,443:31146/TCP`
`rabbitmq NodePort 10.106.25.24 <none> 15672:35506/TCP,25672:11316/TCP`
2. 新建slb监听80和443,slb启用一个虚拟服务器指向ingress-nginx所在的服务器监听后端端口25385和31146
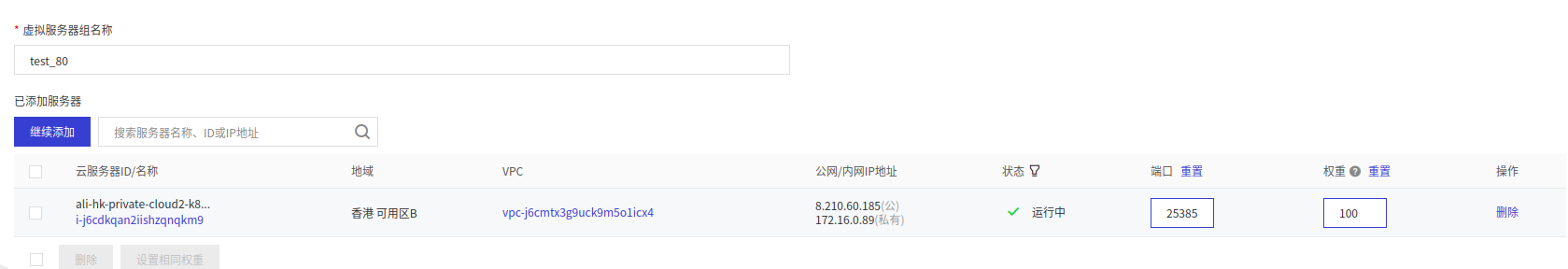
3. 新建ingress,配置域名指向对应服务的svc
```
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: rabbitmq-ui
namespace: crm
annotations:
kubernetes.io/ingress.class: "nginx"
cert-manager.io/cluster-issuer: "letsencrypt-prod"
spec:
rules:
- host: nginx.lwork.com
http:
paths:
- backend:
serviceName: my-nginx
servicePort: 80
path: /
- host: rabbitmq-cloud2.lwork.com
http:
paths:
- backend:
serviceName: rabbitmq
servicePort: 15672
path: /
```
**配置证书后的域名访问,http会强制308跳转到https**
解决:
给ingress添加注解
nginx.ingress.kubernetes.io/ssl-redirect: "false" 取消强制ssl ?????????
nginx.ingress.kubernetes.io/force-ssl-redirect: "false" 取消强制ssl ?????????
二、启用nginx配置stream到ingress-nginx的svc监听的端口上。(当服务器80和443被占用,可以重新监听任何端口,只不过最前面需要一个slb),再转向后端的nginx。
1.系统ubuntu18.04,nginx1.14.0,ingress-nginx,cert-manager,在k8s中跑个nginx容器,域名解析已经指向这台服务器。
2. nginx配置stream指向ingress-nginx.svc的53058和30187
nginx直接使用的apt install,自带stream模块
```
stream {
log_format proxy '$remote_addr $remote_port - [$time_local] $status $protocol '
'"$upstream_addr" "$upstream_bytes_sent" "$upstream_connect_time"' ;
access_log /var/log/nginx/proxy.log proxy;
upstream ingress_80 {
server 10.81.24.51:53058 weight=5 max_fails=3 fail_timeout=30s;
}
upstream ingress_443 {
server 10.81.24.51:30187 weight=5 max_fails=3 fail_timeout=30s;
}
server {
listen 80;
proxy_connect_timeout 3s;
proxy_timeout 3s;
proxy_pass ingress_80;
}
server {
listen 443;
proxy_connect_timeout 3s;
proxy_timeout 3s;
proxy_pass ingress_443;
}
}
```
3. 部署ClusterIssuer
4. 配置ingress
```
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
annotations:
cert-manager.io/cluster-issuer: letsencrypt-prod
kubernetes.io/ingress.class: nginx
kubernetes.io/tls-acme: "true"
name: my-nginx
namespace: crm
spec:
rules:
- host: testnginx.lwork.com
http:
paths:
- backend:
serviceName: my-nginx
servicePort: 80
path: /
```
先验证容器中nginx是否正常,再添加ssl
```
tls:
- hosts:
- testnginx.lwork.com
secretName: testnginx.lwork.com
```
检查cert-manager日志来排错。
三、ingress-nginx.svc监听在80和443,nginx启动800端口,ingress-nginx.svc都转发到800端口(前提是kubeapiserver的端口做过修改- --service-node-port-range=80-61000)
1. 新建svc `kubectl edit svc -n crm crm`
```
spec:
ports:
- port: 80
protocol: TCP
targetPort: 800
sessionAffinity: None
type: ClusterIP
```
2. 新建ingress `kubectl edit ingress -n crm crm`
```
spec:
rules:
- host: bk.mentaricrm.com
http:
paths:
- backend:
serviceName: crm
servicePort: 80
path: /
```
3. nginx新建配置文件
```
server {
listen 800;
server_name bk.mentaricrm.com;
access_log /var/log/nginx/bk.mentaricrm.com.log main;
set $getui $cookie_feVersion;
```
- 笔记
- shell
- 如何才能学好Shell编程之“老鸟”经验谈
- scripts
- 迁移脚本
- centos_install.sh
- https.support.lwork.com.conf
- newbroker.default.lwork.com.conf
- bwnginx.conf
- twnginx.conf
- pre.default.lwork.com.conf
- zabbix_agentInstall
- getcc.sh
- shell脚本调试
- shell学习
- 第一章shell脚本入门
- shell脚本开发的基本规范及习惯
- 脚本规范示例
- 第三章变量的核心知识与实践
- 第四章变量知识进阶和实践
- 4.3 shell变量子串知识及实践
- 4.4 shell特殊扩展变量的知识与实践
- 第五章 变量的数值计算实践
- 第六章 shell脚本的条件测试
- 第七章 if条件的知识与实践
- 第8章 shell函数的基础实践
- 第13章 Shell数组的应用实践
- 经验
- for和while读行的区别
- 一个文件取2个参数
- 重定向正确及错误输出
- linux常用命令
- awk
- 详解
- 例子
- 内置变量
- 实例2
- 实例3
- find/grep
- iostat
- java启动脚本
- ln -s
- nmap
- passwd
- sed
- 详解
- 例子
- ssh-copy-id
- vim
- linux systemd详解
- 常用命令实列
- ss
- rz,sz小文件上传下载
- 文件的合并,排序和分割
- sort,uniq
- sort
- uniq
- cut
- paste
- tr
- curl
- cpu
- scp
- 批量添加注释
- nc
- yarn
- lsof
- tar
- cat
- openssl自签名证书
- pwgen
- logrotate
- 中间件
- mongo
- mongo配置文件详解
- mongo安装
- mongo常用命令
- mongo导入导出
- 导出数据的mongojs
- mongo shell
- mongo异常关闭
- mongo的缺点
- mysql
- 安装
- Gitd
- 主从同步
- 常用命令
- 日志清理
- 连接数,最大并发数,超时
- 错误
- 错误1872
- 错误1236
- 错误1-gitd主从报错
- 一些优化
- 服务器硬件优化
- 编译安装
- mysql配置文件优化
- 根据status优化
- 优化思路
- index
- 查询数据库大小
- ubuntu18.04mysql启动脚本
- pure-ftpd
- rabbitmq
- consul
- redis
- 安装
- 配置
- redis-sentinel
- 常用命令
- supervisor启动redis
- freeipa
- ftp
- 错误530根本原因和解决方法
- vsftp
- sftp
- JDK
- java参数
- zabbix
- 安装
- nginx
- 基础
- 1.基础web配置
- 2.nginx的日志格式
- 3.Nginx的请求限制
- 4.Nginx访问控制
- 进阶
- 1.静态资源web服务
- 2.Nginx作为代理服务
- 3.负载均衡
- 4.rewrite模块
- 5.Geoip
- location与proxy_pass
- proxy_set_header参数
- add_header
- 安装
- 4XX5XX重定向
- Nginx resolver explained
- 关于防止自己网页内容被别人iframe的问题
- nginx全局变量
- nginx错误代码
- 平滑升级nginx
- nginx相关资料网站
- nginx配置下载目录
- 反向代理并发数
- php
- 安装centos6,7
- xtrabackup
- apache
- 常用工具
- SSL证书在线工具SSL
- wordpress
- kafka
- nssm
- GoCD
- gocd简介
- gocd一些概念
- gocd客户端环境变量
- 建立一个piplines
- gocd添加nodejs
- supervisor
- mongo,mysql,hadoop比较
- screen
- python
- minio-私有存储桶
- kubernetes
- YAML格式简单说明
- k8s集群常用命令
- 概念
- k8s组件
- 对象
- workloads
- pods
- overview
- pod lifecycle
- init containers
- env向容器暴露pod信息
- controllers
- rs
- deployments
- daemonset
- StatefulSet
- service
- ingress
- volumes及configmap
- pv和pvc
- serviceaccount及认证
- dashboard及分级授权
- flannel&calico
- 调度器,预选策略及优先函数
- 资源指标API及自定义指标API
- helm
- k8s最佳实践
- 配置kubelet
- 简单命令定位问题
- k8s中日志收集-1
- k8s中日志收集-2
- lxcfs
- v1.24以后镜像问题
- 单控制节点集群v1.24以后适用
- 单控制节点集群v1.24前适用
- K8s.1.11.x阿里云安装HA版
- 国内k8s安装指定版本
- 发布及回滚
- 检查yaml文件格式
- pod分配到指定节点
- k8s跨集群访问
- 在docker中查看对应k8s容器日志
- cert-manager
- 问题定位技巧:容器内抓包
- 为容器设置启动时要执行的命令及其入参
- deploy.yaml文件实例
- kube/config
- 系统守护进程预留资源
- k8s集群证书pki过期处理
- pod跑java时内存的运用
- 从外部访问k8s中的pod
- HPA实战
- Docker
- Docker常用命令
- 基本概念
- 镜像
- 容器
- 仓库
- 安装 Docker
- Ubuntu
- Centos
- 镜像加速器
- 使用镜像
- 获取镜像
- 使用 Dockerfile 定制镜像
- Dockerfile 指令详解
- COPY 复制文件
- CMD 容器启动命令
- ENTRYPOINT 入口点
- ENV
- 其他命令
- 参考文档
- Alpine制作JDK8镜像
- Dockerfile示例
- 访问仓库
- nexus
- 最佳实践
- 镜像删除
- 清理docker磁盘空间
- docker容器日志管理
- 镜像基础上构建镜像
- git
- 公钥私钥免登
- 常用命令
- git pull
- git升级
- jenkins
- jenkins使用git
- 设置构建作业
- General
- Source Code Management
- Build Traggers
- Build Environment
- Build
- Post-build Actions
- 高级构建
- 参数化构建作业
- prometheus
- 监控原则
- 第一章 采集数据
- HPA
- meterics-server
- custom metrics
- kube-state-metrics
- node-exporter
- 第二章 prometheus
- prometheus概述
- prometheus基本架构
- prometheus安装
- prometheus的配置和服务发现
- scrape_configs
- kubernetes_sd_config
- relabel_config
- relabel_config例子
- 服务发现配置
- alertmanager_config
- alerting
- configuration
- route
- receivers
- inhibits_rules
- 第三章 展示与告警
- 第四章 PromQL
- rate,irate和delta的区别
- prometheus-operator
- maven
- maven命令
- maven仓库配置
- openstack
- 网络基础
- 计算机网络原理
- 一个URL请求的过程
- 2.记录
- 3.数据链路层
- 4.网络层
- 网络常用命令
- 命令
- iptables
- nc
- ipset
- mtr
- ss
- lsof
- ip
- 抓包
- tcpdump
- 网络排错与观察
- netstat
- traceroute
- dig与nslookup
- 计算机网络协议
- 负载均衡总结性说明
- NAT
- Tinc
- ubuntu
- ubuntu-var-log-下各个日志文件
- apt和dpkg
- systemctl详解
- 关闭系统更新,有些更新可能影响运行的程序
- ubuntu常用命令
- 基础工具journalctl命令
- za
- 恢复阿里云物理备份
- 域名证书申请和更换
- 正则表达式常用
- 服务器上排查问题得头5分钟
- windows
- winserver关闭事件跟踪程序
- windows常用命令
- win10企业LTSC版激活
- windows通过网卡只开80端口
- debug-tools
- win10-1903及以上版本Realtek高清晰音频管理器
- 彻底解决WPS Office Expansion tool弹出问题
- services延迟启动时间修改
- windows服务器定时重启
- windows sc命令
- 防火墙概述
- iptables
- 简单说明
- 例子
- 项目一
- DevOps简介
- 项目介绍
- 高并发内核优化
- gitlab
- gitlab社区和企业版本区别
- gitlab社区版安装
- gitlab指定版本安装
- gitlab安全设置
- gitlab的备份和恢复
- gitlab容器化安装
- jenkins
- jenkins安装
- ubuntu 16.04 install jenkins
- ubuntu 20.04 install jenkins
- jenkins使用git
- jenkins配置第一个项目
- jenkins发布及制作jar镜像
- jenkins安全策略
- gocd
- gocd安装
- k8s中gocd的server和agent模板
- gocd配置第一个项目
- 脚本
- gocd+ldap
- nexus
- 安装和配置
- freeipa
- 介绍
- 安装
- freeipa集成ocserv
- VPN
- 原理
- vpn部署ocserv
- k8s
- k8s高可用集群
- DNSmasq
- SNIproxy
- Tinc
- prometheus
- 简介
- helm安装prometheus
- 采集数据概览
- 采集数据node-exporter
- 采集数据kube-state-metrics
- 采集数据cadvisor和apiservers
- 指标汇总展示
- 监控
- nginx+lua+waf
- 项目二
- 简介
- nacos
- 简介
- nacos配置管理功能
- tengine
- java
- java参数说明及优化
- github快速访问
- amd和arm区别
- AWS
- 负载均衡ALB
