[TOC]
# traefik 2.X版本使用
因为traefik 1.X 和 2.X 的版本区别太大了,而且还不兼容,所以单独记录一下安装和使用过程
### 安装traefik 2.2
traefik 2.X 版本在定义路由的时候,没有使用k8s自带的ingress资源,而是使用了自定义的`ingressroutes`资源,所有安装步骤和官网保持一致。
安装步骤要按照顺序一个一个执行。
##### 1) 创建自定义资源
definition.yaml
~~~
apiVersion: apiextensions.k8s.io/v1beta1
kind: CustomResourceDefinition
metadata:
name: ingressroutes.traefik.containo.us
spec:
group: traefik.containo.us
version: v1alpha1
names:
kind: IngressRoute
plural: ingressroutes
singular: ingressroute
scope: Namespaced
---
apiVersion: apiextensions.k8s.io/v1beta1
kind: CustomResourceDefinition
metadata:
name: middlewares.traefik.containo.us
spec:
group: traefik.containo.us
version: v1alpha1
names:
kind: Middleware
plural: middlewares
singular: middleware
scope: Namespaced
---
apiVersion: apiextensions.k8s.io/v1beta1
kind: CustomResourceDefinition
metadata:
name: ingressroutetcps.traefik.containo.us
spec:
group: traefik.containo.us
version: v1alpha1
names:
kind: IngressRouteTCP
plural: ingressroutetcps
singular: ingressroutetcp
scope: Namespaced
---
apiVersion: apiextensions.k8s.io/v1beta1
kind: CustomResourceDefinition
metadata:
name: ingressrouteudps.traefik.containo.us
spec:
group: traefik.containo.us
version: v1alpha1
names:
kind: IngressRouteUDP
plural: ingressrouteudps
singular: ingressrouteudp
scope: Namespaced
---
apiVersion: apiextensions.k8s.io/v1beta1
kind: CustomResourceDefinition
metadata:
name: tlsoptions.traefik.containo.us
spec:
group: traefik.containo.us
version: v1alpha1
names:
kind: TLSOption
plural: tlsoptions
singular: tlsoption
scope: Namespaced
---
apiVersion: apiextensions.k8s.io/v1beta1
kind: CustomResourceDefinition
metadata:
name: tlsstores.traefik.containo.us
spec:
group: traefik.containo.us
version: v1alpha1
names:
kind: TLSStore
plural: tlsstores
singular: tlsstore
scope: Namespaced
---
apiVersion: apiextensions.k8s.io/v1beta1
kind: CustomResourceDefinition
metadata:
name: traefikservices.traefik.containo.us
spec:
group: traefik.containo.us
version: v1alpha1
names:
kind: TraefikService
plural: traefikservices
singular: traefikservice
scope: Namespaced
---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: traefik-ingress-controller
rules:
- apiGroups:
- ""
resources:
- services
- endpoints
- secrets
verbs:
- get
- list
- watch
- apiGroups:
- extensions
resources:
- ingresses
verbs:
- get
- list
- watch
- apiGroups:
- extensions
resources:
- ingresses/status
verbs:
- update
- apiGroups:
- traefik.containo.us
resources:
- middlewares
- ingressroutes
- traefikservices
- ingressroutetcps
- ingressrouteudps
- tlsoptions
- tlsstores
verbs:
- get
- list
- watch
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: traefik-ingress-controller
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: traefik-ingress-controller
subjects:
- kind: ServiceAccount
name: traefik-ingress-controller
namespace: default
~~~
##### 2) 创建traefik使用的service资源
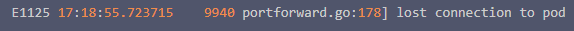
> 根据官网的第四个步骤,需要使用一个 kubectl port-forward 的端口转发的操作,但是在我的环境中执行端口转发的时候有报错,所以我要修改官网service.yaml部分,直接使用 NodePort 方式将traefik绑定在节点上,而不是用代理转发
> 
service.yaml
~~~
apiVersion: v1
kind: Service
metadata:
name: traefik
spec:
type: NodePort
ports:
- protocol: TCP
name: web
port: 8000
nodePort: 80 #这里绑定到了节点的8000端口
- protocol: TCP
name: admin
port: 8080
nodePort: 8080 #这里绑定到了节点的8000端口
- protocol: TCP
name: websecure
port: 4443
nodePort: 443 #这里绑定到了节点的8000端口
selector:
app: traefik
---
# 这个下面的部分是官网中用于测试 traefik 是否正常使用的测试容器
apiVersion: v1
kind: Service
metadata:
name: whoami
spec:
ports:
- protocol: TCP
name: web
port: 80
selector:
app: whoami
~~~
##### 3) 创建traefik使用的service资源
部署`traefik`和用于测试`whoami`容器
deployment.yaml
~~~
apiVersion: v1
kind: ServiceAccount
metadata:
namespace: default
name: traefik-ingress-controller
---
kind: Deployment
apiVersion: apps/v1
metadata:
namespace: default
name: traefik
labels:
app: traefik
spec:
replicas: 1
selector:
matchLabels:
app: traefik
template:
metadata:
labels:
app: traefik
spec:
serviceAccountName: traefik-ingress-controller
containers:
- name: traefik
image: traefik:v2.2
args:
- --api.insecure
- --accesslog
- --entrypoints.web.Address=:8000
- --entrypoints.websecure.Address=:4443
- --providers.kubernetescrd
- --certificatesresolvers.myresolver.acme.tlschallenge
- --certificatesresolvers.myresolver.acme.email=foo@you.com
- --certificatesresolvers.myresolver.acme.storage=acme.json
# 这一行是用于测试的,可以屏蔽掉,这个网址要翻墙才能访问,所以我随手屏蔽了
#- --certificatesresolvers.myresolver.acme.caserver=https://acme-staging-v02.api.letsencrypt.org/directory
ports:
- name: web
containerPort: 8000
- name: websecure
containerPort: 4443
- name: admin
containerPort: 8080
---
kind: Deployment
apiVersion: apps/v1
metadata:
namespace: default
name: whoami
labels:
app: whoami
spec:
replicas: 2
selector:
matchLabels:
app: whoami
template:
metadata:
labels:
app: whoami
spec:
containers:
- name: whoami
image: containous/whoami
ports:
- name: web
containerPort: 80
~~~
##### 4) 编写自定义转发资源IngressRouters
ingressrouters.yaml
~~~
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: simpleingressroute
namespace: default
spec:
entryPoints:
- web
routes:
- match: Host(`your.example.com`) && PathPrefix(`/notls`)
kind: Rule
services:
- name: whoami
port: 80
---
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:
name: ingressroutetls
namespace: default
spec:
entryPoints:
- websecure
routes:
- match: Host(`your.example.com`) && PathPrefix(`/tls`)
kind: Rule
services:
- name: whoami
port: 80
tls:
certResolver: myresolver
~~~
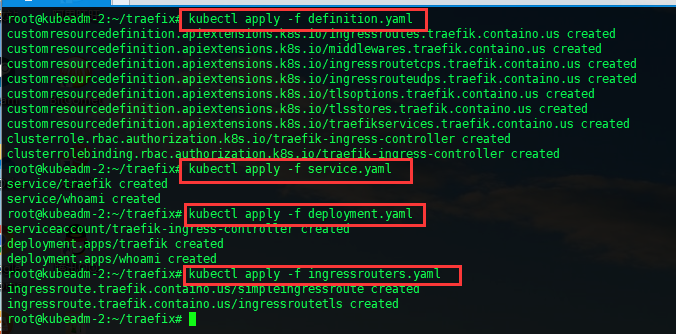
##### 5)查看执行结果
##### 6)检查是否能正常访问
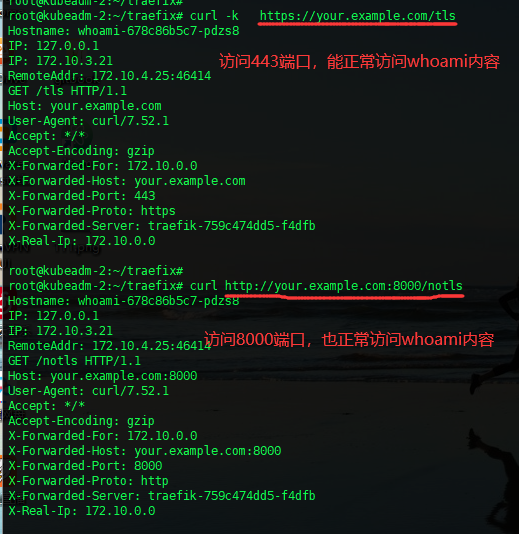
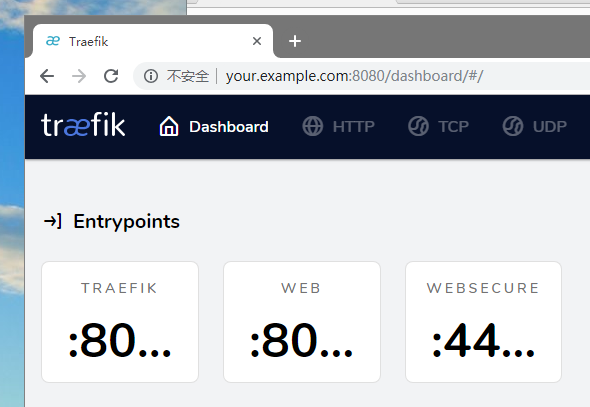
在 hosts中添加dns解析 192.168.222.8 your.example.com
- 一、K8S的安装
- 1.1 安装环境
- 1.2 问题汇总
- 1.3 事前准备
- 1.4 安装配置负载均衡
- 1.5 安装K8S软件
- 1.6 初始化kubeadm
- 1.7 添加控制节点
- 1.8 添加计算节点
- 1.9 安装故障问题处理
- 1.10 安装管理dashboard
- 1.11 编写测试Pod
- 1.12 从外部访问集群中的Pod
- 1.13 部署metrics-server指标采集
- 二、Pod管理
- 2.1 Pod 资源需求和限制
- 2.2 Init 容器
- 2.3 Pod 健康检查(探针)和重启策略
- 2.4 Pod 生命周期(钩子Hook)
- 2.5 静态Pod
- 2.6 初始化容器(init container)
- 2.7 资源限制
- 三、资源控制器
- 3.1 Deployment
- 3.2 StatefulSet
- 3.3 DaemonSet
- 3.4 Job
- 3.5 定时任务
- 3.6 准入控制器
- 3.7 自动伸缩
- 3.8 ReplicaSet
- 四、存储
- 4.1 Secret 管理敏感信息
- 4.2 ConfigMap 存储配置
- 4.3 Volume
- 4.4 PV
- 4.5 PVC
- 4.6 StorageClass
- 4.7 暴露宿主机信息给Pod
- 五、服务Service
- 5.1 Service 资源
- 5.2 服务发现
- 5.3 服务暴露
- 5.4 Ingress 资源
- 5.5 Ingress 专题
- 5.6 traefik 2.X版本使用
- 六、认证、授权、准入控制
- 6.1 服务账户
- 6.2 LimitRange资源与准入控制器
- 6.3 ResourceQuota 资源与准入控制器
- 七、Helm
- 7.1 Helm 安装
- 八、 istio
- 8.1 istio 介绍
- 8.2 iotis 安装
- 九、calico
- 9.1 两种网络模式
- 9.2 全互联模式 与 路由反射模式
- 9.3 BGP跨网段(大型网络)
- 十、Ingress
- 10.1 安装 LoadBalancer
- 10.2 部署 ingress-nginx
- 10.3 Ingress-nginx 的使用
- 10.4 开启TCP和UDP
- 使用中的问题
- CSI Node问题
